ScreenOS 5.4.0r26.0
Problem:
SIP funktioniert zwar, die NS204 läßt jedoch keine SIP Keep Alives durch. Nur die „ordentliche“ SIP Registrierung klappt.
Beachte auch http://www.krakovic.de/voip-und-sip-beispiel-einer-sip-session/
NS204_EF_1(M)-> get dbuf str
****** 07147.0: <Trust/ethernet1> packet received [32]******
ipid = 6786(1a82), @d780a110
ipsec decrypt engine released, auth check pass!
packet is decrypted
ipsec decrypt done
put packet(5883fbc) into flush queue.
packet passed sanity check.
ethernet1:10.136.172.201/5060->195.222.249.61/5060,17<Root>
existing session found. sess token 4
flow got session.
flow session id 126431
vsd 0 is active
packet dropped, application error
remove packet(5883fbc) out from flush queue.
Lösung:
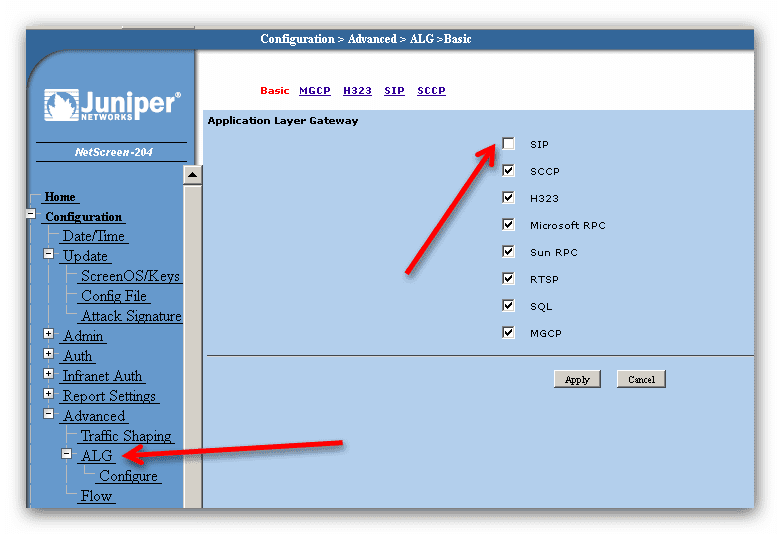
ALG für SIP ausschalten!
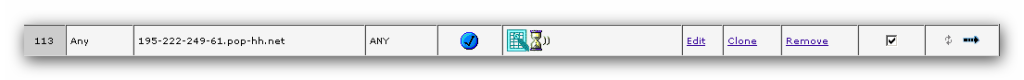
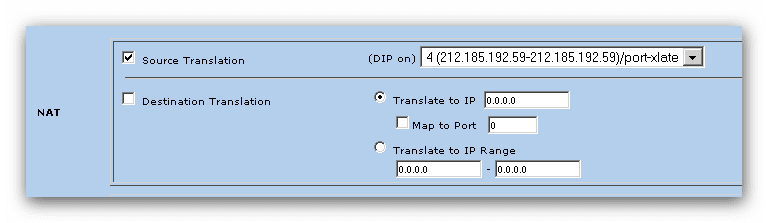
Eine ausgehende Regel zum SIP Proxy mit einer DIP einrichten:
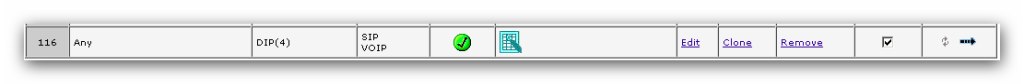
Dann eine Regel von Untrust zu Trust anlegen:
Beachte auch http://kb.juniper.net/InfoCenter/index?page=content&id=KB4872&pmv=print
Juniper bietet diese Lösung an:
SIP Application is not working. From the debugs, the SIP application is using non-standard ports.
By default, the SIP Application Layer Gateway (ALG) on the firewall expects the following standard ports:
pep-> get service SIP
Name: SIP
Category: other ID: 0 Flag: Pre-defined
Transport Src port Dst port ICMPtype,code Timeout(min|10sec*) Application
udp 0/65535 5060/5060 1 SIP
tcp 0/65535 5060/5060 30 SIP
In the ‚debug flow‘ output that was run during the SIP call attempt, the following was captured.
172.17.8.6/13ce, 13ce represents the port number in HEX, which translates to 5070:
**st: <Private|ethernet2/2.113|Root|71> 399c11c: 0:14.23.242.84/1350->172.17.8.6/13ce,17,384
****** 15099885.0: <Private-MT/ethernet2/2.113> packet received [384]******
ipid = 0(0000), @0399c11c
packet passed sanity check.
flow packet already have session.
flow session id 522781
vsd 0 is active
packet dropped, application error
This response packet for the SIP Invite was dropped with an application error.
Solution:
The solution is to configure the policy to customize the SIP ALG on the Juniper Firewall to recognize the non-standard SIP ports:
set service SIP-5070 protocol udp src-port 1-65535 dst-port 5070-5070
set policy id 200 from Trust to Untrust any any SIP-5070 permit
set policy id 200 application SIP <----------------
The command „set policy application SIP“ along with „set policy from Trust to Untrust any any SIP-5070 permit“ effectively allows the firewall to recognize the port 5070 as part of SIP traffic and to handle it accordingly by the ALG.
In the WebUI, on the policy defined for the SIP traffic, click the Application pull-down and select SIP.